Month: May 2017
What you need to know about WannaCry
On Friday, May 12, 2017, a ransomware attack known as “WannaCry” (detected by ESET as Win32/Filecoder.WannaCryptor.D) began to spread across the globe at unprecedented scale and speed.
For our customers: Yes, ESET detects and blocks the WannaCryptor.D threat and its variants. ESET’s network protection module (in ESET Endpoint Security) also blocks the exploit (known as EternalBlue) used to spread it at the network level. Attempts to exploit the leaked vulnerability had already been detected, reported on, and stopped well before this particular malware was even created. On Friday, ESET increased the protection level for this particular threat via updates to our detection engine. (For more information on ESET products that prevent a WannaCry infection, view our Customer Advisory.)
The rapidly spreading WannaCry that utilizes the leaked United States National Security Agency (NSA) exploit, EnternalBlue, was released last month by a hacker collective known as Shadow Brokers.
When WannaCry touches a user’s computer, it encrypts its files, and tells the victim to pay in Bitcoin in order to retrieve those files. The ransom demanded for decryption of the files appears to be about $300. It then will use the EternalBlue exploit to access unpatched machines. (For a real-time check of the amounts that the malicious actors have received in Bitcoin funds, go here.)
Reports of WannaCry started in Spain’s telecom sector and quickly spread from that point to healthcare organizations in the U.K., plus various commercial websites, entire enterprise sites, and just about every type of network in between. People from around the world posted screenshots of the malware from computers in offices, hospitals and schools.
As far as we can tell, the attack is continuing to spread. Please follow these steps to help keep your business protected in the wake of WannaCry.
Ensure your Windows machines are up to date:
- Patches can be difficult to deploy across the entire network. However, you’ll want to install this one. It has been available since mid-April and actually stops the exploit from gaining a foothold in your environment. The patch listing for the entire listing of the Equation Group files can be located here.
- Use anti-malware software: This is a basic but critical component. Just because it’s a server, and it has a firewall, does not mean it does not need anti-malware: it does. Always install a reputable anti-malware program. (And one that protects against the EternalBlue exploit.)
- Back up files: For companies hit by ransomware that do have current backups, the attack is not nearly as damaging. Make sure you always back up data, and regularly check to make sure your backup systems are working properly.
ESET has been using its Threat Intelligence and appropriate YARA rules that identified the characteristics pertaining to the NSA’s leaked exploitation files. There have been many detections of these objects. Within the last few weeks, we have seen increased activity, and do not expect it to stop anytime soon.
Our security research teams around the globe are working 24/7 and continuing to track, monitor (both EternalBlue and WannaCry) and report on what we find. We are releasing our most up-to-date research on Welivesecurity.com, and sharing via our social channels.
Learn how ESET protects you against ransomware here. To see how ESET protects businesses, click here.
Follow @ESET on Twitter and/or Facebook for updates on this topic.
(Media requests, please contact PR@eset.com)
SonicWall Protects Customers from the Latest Massive WannaCry Ransomware Attack
MAY 12, 2017 BY BROOK CHELMO
Note: This blog was updated on Monday, May 15.

First, if you are a SonicWall customer and you are using our Gateway Anti-Virus, Intrusion Prevention service, and Capture Advanced Threat Protection then your SonicWall firewall has been protecting your network from WannaCry ransomware and the worm that spreads it since 17 April, 2017. Since the release of the first version of the code, we have identified several new variants and have released additional counter measures. We will continue to update this blog as our Capture Labs research team uncovers more information and as additional protection is automatically rolled out to our customers’ firewalls.
Here’s more:
The Attack
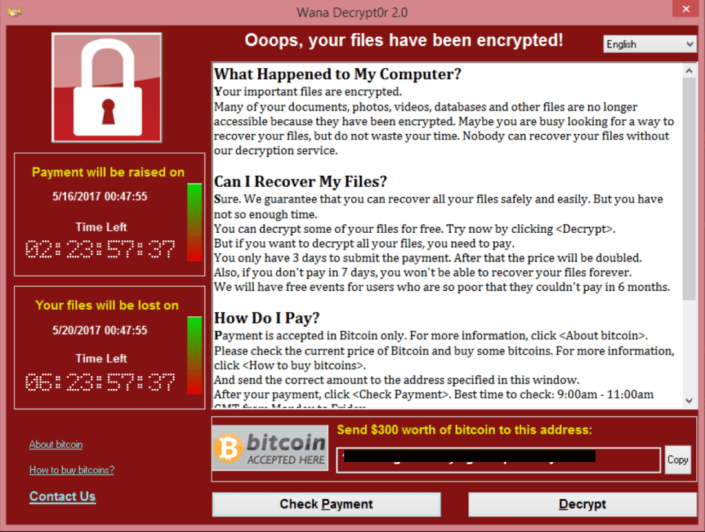
This massive ransomware attack became infamous by shutting down a number of hospitals in the UK’s National Health Service (NHS) system and thus preventing patients from receiving critical care. The attack hit over 100 countries across the world with an untold number of victims. WannaCry is a combination of a Trojan/ransomware and a worm that leverages an SMB file sharing protocol exploit named EternalBlue. The Shadow Brokers leaked EternalBlue in April 2017 as part of a bigger dump of NSA developed exploits. This exploit affects various versions of Microsoft Windows operating systems, including a number of versions that are in end-of-life status. Although Microsoft released a large number of patches on March 14 to address this vulnerability, the attack remains dangerous as many organizations have not applied the patch.
The first version of the worm/ransomware package had a kill switch that was accidently used to disable the worm feature which slowed its advance on Friday, 12 May 2017. However, new variants are appearing in the wild without this weakness. While the first version of the worm code can no longer spread the ransomware code, systems encrypted by WannaCry 1.0 will remain encrypted. Unfortunately, there is no known decryption method to recover files affected by WannaCry without paying cyber criminals (which is not advised).
Since Friday, 12 May 2017, SonicWall’s Capture Labs released six new signatures to block all known versions of WannaCry. It is also worth noting that SonicWall security services on the firewall have built-in protections against the many components of this code, ranging from blocking contact with WannaCry Command and Control (C&C) servers to blocking attempts at exploitation of any unpatched SMB Microsoft vulnerabilities (such as EternalBlue).
The Protection
SonicWall Capture Labs analyzed the EternalBlue attack in mid-April immediately after the Shadow Brokers file dump and rolled out protection for all SonicWall firewall customers well in advance of the first public attack. All known versions of this exploit can be blocked from SonicWall protected networks via active next-generation firewall security services.
As a SonicWall customer, ensure that your next-generation firewall has an active Gateway Security subscription to receive automatic real-time protection from known ransomware attacks such as WannaCry. Gateway Security includes Gateway Anti-virus (GAV), Intrusion Prevention (IPS), Botnet Filtering, and Application Control. This set of technology has signatures against WannaCry (part of GAV), protections against vulnerabilities outlined in Microsoft’s security bulletin MS17-010 (part of IPS), and it blocks communication with the C&C servers where WannaCry’s payload comes from (part of botnet filtering).
Since SonicWall Email Security uses the same signatures/definitions as Gateway Security, we can effectively block the emails that deliver the initial route to infection. Ensure all email security services are also up to date to block malicious emails. Since 65% of all ransomware attacks happen through phishing emails, this needs to be a major focus when giving security awareness training. Additionally, customers with SonicWall Content Filtering Service should activate it to block communication with malicious URLs and domains, which works in a similar way Botnet filtering disrupts C&C communication.
As a best practice always deploy Deep Packet Inspection of all SSL/TLS (DPI-SSL) traffic since more than 50% of malware is encrypted. This will enable your SonicWall security services to identify and block all known ransomware attacks. Enabling DPI-SSL also allows the firewall to examine and send unknown files to SonicWall Capture Advanced Threat Protection for multi-engine processing to discover and stop unknown ransomware variants.
View our webpage to learn more on how SonicWall protects against ransomware.
The most recent list of GAV/IPS signatures against EternalBlue and WannaCrypt as of 14 May 2017 at 11:45 AM PST

What’s Next
The party behind this attack has already released several variations of this attack for which we have established protections in place (see above). To ensure you are safe from newly developed updates and similar copycat attacks, first apply the Windows patch provided by Microsoft listed in the resources section. Second, apply Capture Advanced Threat Protection (Capture ATP), SonicWall’s multi-engine network sandbox, to examine suspicious files coming into your network to discover and stop the latest threats just as we did with Cerber ransomware. Enable the service’s block until verdict feature to analyze all files at the gateway to eliminate malware before it can enter your network. Additionally, Capture Labs will continue to email customers Sonic Alerts on new threats.
Finally, phishing emails are the most common delivery mechanism for ransomware. It is possible that future variants of this ransomware will be delivered via emails. SonicWall’s email security solution uses Advanced Reputation Management (ARM) to inspect not only the sender IP but also the message content, embedded URLs and attachments. In addition, make sure you enable SPF, DKIM and DMARC advanced email authentication to identify and block spoofed emails and protect from spam and phishing attacks. For the best possible protection against such attacks, deploy SonicWall’s email security solution with Capture ATP service to inspect every email attachment in a multi-engine sandbox environment.
Apart from SonicWall security protections in place (listed above), as a best practice we recommend to disallow or block inbound SMB traffic (TCP 445, UDP ports 137-138, and TCP 139) and RDP traffic coming from the internet on edge-facing Firewalls. If such access is required, implement secure remote access solutions like IPsec or SSL-VPN with proper authentication mechanisms in place.
Apply vulnerability patches on servers and PCs as recommended in Microsoft MS17-010 bulletin (listed above and below), disable SMBv1 communication (limit access via SMBv2/v3), as well as monitor for any suspicious activity on TCP 445.
Resources
- Microsoft’s Customer Guidance for WannaCrypt attacks
- Microsoft Security Bulletin MS17-010
- SonicWall Gateway Anti-Virus Information
- SonicWall Capture Advanced Threat Protection Service Information
- SonicWall Email Security
- SonicWall Content Filtering ServiceLearn More Watch our webcast Stopping WannaCry Ransomware
IHG CONFIRMS SECOND CREDIT CARD BREACH IMPACTING 1,000-PLUS HOTELS
by Chris Brook, April 18, 2017

Holiday Inn image via phalinn‘s Flickr photostream, Creative Commons
In what’s becoming a familiar refrain to guests, InterContinental Hotels Group, said [in mid-April] that payment card systems at more than 1,000 of its hotels had been breached.
It’s the second breach that IHG, a multinational hotel conglomerate that counts Holiday Inn and Crowne Plaza among its chains, has disclosed this year. The company acknowledged in February that a credit card breach affected 12 of its hotels and restaurants.
In a notice published to its site [mid-April] the company said a second breach occurred at select hotels between Sept. 29 and Dec. 29 last year. IHG says there’s no evidence payment card data was accessed after that point but can’t confirm the malware was eradicated until two to three months later, in February/March 2017, when it began its investigation around the breach.
Like most forms of payment card malware these days, IHG said the variant on their system siphoned track data – customers’ card number, expiration date, and internal verification code – from the magnetic strip of cards as they were routed through affected hotel servers.
The hotelier said the first breach also stemmed from malware found on servers used to process credit cards, but from August to December 2016. That breach affected hotels, along with bars and restaurants at hotels, such as Michael Jordan’s Steak House and Bar at InterContinental Chicago and the Copper Lounge at Intercontinental Los Angeles.
IHG didn’t state exactly how many properties were affected by the second breach but that customers can use a lookup tool the company has posted to its site to search for hotels in select states and cities. IHG gives a timeline for each property and says hotels listed on the tool “may have been affected.”
A cursory review of hotels in the lookup tool suggests far more than a dozen – more than a thousand – hotels, were affected by the malware.
IHG says that since the investigation is ongoing the tool may be updated periodically. Some properties, for a reason not disclosed, elected to not participate in the investigation, IHG said.
While the company operates 5,000 hotels worldwide this most recent breach affects mostly U.S.-based chains. One hotel in Puerto Rico, a Holiday Inn Express in San Juan, is the only non-U.S. property that was hit by malware this time around, IHG claims.
The company said it began implementing a point-to-point encryption payment solution – technology that can reportedly prevent malware from scouring systems for payment card data last fall. The hotels that were hit by this particular strain of malware had not yet implemented the encryption technology, IHG claims.
The news comes as an IHG subsidiary, boutique hotel chain Kimpton, is fighting a class action court case that alleges the company failed to take adequate and reasonable measures to protect guests payment card data.
The chain said it was investigating a rash of unauthorized charges on cards used at its locations last summer. It eventually confirmed a breach in late August that involved cards used from Feb. 16, 2016 and July 7, 2016 at nearly all of its restaurants and hotels.
Bloomberg reported that Lee Walters, the plaintiff in the case against Kimpton, failed to plead all relevant factors. The judge overseeing the case, Judge Vince Chhabria of the U.S. District Court for the Northern District of California, dismissed California state fraud claims last week. Chhabria is allowing claims of implied contract, negligence, and California unfair business practices to continue however.
Sneaky Exploit Allows Phishing Attacks From Sites That Look Secure

by Lily Hay Newman, Security for Wired
April 18, 2017
PHISHING ATTACKS CAN make even crusading technovangelists paranoid. One wrong click can put you out a ton of cash, or cause a corporate breach. And they evolve constantly. Case in point: A cunning new exploit makes malicious phishing websites appear to have the same URL as known and trusted destinations.
You know by now to check your browser while visiting a site to be sure it sports the little green padlock indicating TLS encryption. See it and you know no one can eavesdrop on any data you submit—an especially important consideration for financial and healthcare sites. But a malicious site that can impersonate a legit URL and depict that padlock leaves precious few tip-offs that you’re dealing with an imposter.
Ecce Homograph
This particular vulnerability takes advantage of the fact that many domain names don’t use the Latin alphabet (think Chinese characters or Cyrillic). When English-based browsers run into those URLs, they use an encoder called Punycode to render each character from a standardized library of character codes maintained by Unicode, the standards body for text online. This exploit takes advantage of that conversion process; phishers can appear to spell out a familiar domain name using a different URL and web server. Attackers who trick people into loading the fake page could more easily convince them to answer questions or provide personal information because the site seems trustworthy.
These kinds of URL character manipulations, called homograph attacks, started years ago, and groups like the Internet Assigned Numbers Authority work with browser developers to create defenses, including Punycode itself, that make URL spoofing more difficult. But new twists on the attack still crop up. Web developer Xudong Zheng reported this exploit to Google and Mozilla in January and demonstrated it publicly on Friday, creating a fake Apple.com website that appears legitimate and secure in unpatched browsers.
Apple Safari, Microsoft Edge, and Internet Explorer protect against this attack. A Chrome fix arrives in Version 59 this week, but Firefox developer Mozilla continues weighing whether to release a patch. The organization did not return a request for comment.
Until then, you can check the validity of sites by copying and pasting the URLs into a text editor. A spoofed URL only appears familiar, and actually uses an address beginning “www.xn--” that you can see outside the browser bar. Zheng’s fake Apple site, for example, uses the address https://www.xn--80ak6aa92e.com. All Zheng need to do to get the trusted “https” status was apply for TLS encryption from an entity like Let’s Encrypt.
Firefox users also can protect themselves by changing their settings so the address bar only shows the Punycode addresses. Load the phrase “about:config” into your address bar, search for “network.IDN_show_punycode” in the attribute list that appears, right-click on the only result, and choose “Toggle” to change the preference value from “false” to “true.”
Go Phish
Given phishers’ love of domains like www.app1e.com, the Punycode trick seems like a powerful attack. But Aaron Higbee, chief technology officer at the phishing research and defense company PhishMe, says his company hasn’t found any instances of it appearing in the wild. The company also has not found the tools to execute it in any of the pre-fab phishing kits it examines on the dark web.
That’s not to say the exploit isn’t out there somewhere, but Higbee says phishers may not find it reliable because browser autofill mechanisms and password managers won’t autocomplete on spoofed sites. Such tools know, even if users do not, when a URL is not familiar. “There’s going to be a technical control for every phishing technique and eventually that control will be outwitted,” says Higbee. “Phishing lives in that space.”
With the attack publicized, you may see an uptick in its use and further research into even more creative versions. So until that Chrome update comes through, keep a close eye on your URLs—and anything weird on the websites they purport to show you.
SOLUTION BRIEF: HOW TO PROTECT AGAINST RANSOMWARE
Eight best practices to prevent your data from being held hostage
 Brief courtesy of our trusted security partner SonicWall
Brief courtesy of our trusted security partner SonicWall
Ransomware is a term used to describe malware that denies access to data or systems unless a ransom is paid to a cybercriminal. Every organization is susceptible to ransomware attacks. Fortunately, there are many steps you can take to minimize your organization’s risk. Here are eight best practices to protect your organization against ransomware attacks.
- Training and awareness
User training and awareness is paramount, and the first step to safeguard against ransomware. User instruction should include:
- Treat any suspicious email with caution
- Look at the domain name that sent the email
- Check for spelling mistakes, review the signature and the legitimacy of the request
- Hover on links to check where they lead to and if any URL seems suspicious, directly type the website or look it up on search engines vs. clicking the link in the email
- Email security
You should deploy an email security solution that scans all attachments besides filtering for spyware and spam. Along with periodic user training and risk assessments, you should also conduct phishing vulnerability tests.
- Anti-malware
Whether personal or corporate devices, endpoints are particularly at risk if they are not managed by IT, or don’t have the right anti-malware protection. Most anti-virus solutions are signature-based, and prove ineffective if not updated regularly. The newer ransomware variants are uniquely hashed and thereby undetectable using signature-based techniques.
Many users also turn off their virus scans so that it doesn’t slow their system down. To address these limitations, there are endpoint security solutions that use advanced machine learning and artificial intelligence to detect malware. They also have a small footprint, causing minimal performance overhead.
- Mobile endpoints
Management of endpoints is also a growing challenge as devices with multiple form factors and operating systems are introduced to the network. Mobile devices are particularly vulnerable as noted in the 2016 Dell Security Annual Threat Report with emerging ransomware threats on the Android™ platform. Choosing a solution that is able to automate patching and version upgrades in a heterogeneous device, OS and application environment, will go a long way in addressing a range of cyberthreats including ransomware.
For remote users who are outside the enterprise firewall perimeter, VPNbased access should not only establish a secure connection but also conduct a level of device interrogation to check for policy compliance on the endpoint. If an endpoint does not have the required security updates then it will not be allowed on the network or it will be granted access to only a limited set of resources.
Specifically, for Android mobile device users, the following steps are recommended:
- Do not root the device, as it exposes the system files for modifications
- Always install apps from Google Play store, as apps from unknown sites or stores can be fake and potentially malicious
- Disable installation of apps from unknown sources
- Allow Google to scan the device for threats
- Take care when opening unknown links received in SMS or emails
- Install third-party security applications that scan the device regularly for malicious content
- Monitor which apps are registered as Device Administrators
- For corporate-managed devices, create a blacklist of disallowed apps
- Network segmentation
Most ransomware will try to spread from the endpoint to the server/storage where all the data and mission critical applications reside. Segmenting the network and keeping critical applications and devices isolated on a separate network or virtual LAN can limit the spread.
- Backup and recovery
Another safeguard against having to pay ransom is a robust backup and recovery strategy. Back up data regularly. There will be less data loss in case of infection if there is a remote backup. Depending on how quickly the compromise is detected, how far it has spread and the level of data loss that is acceptable, recovery from a backup could be a good option. However, this calls for a smarter backup strategy that is aligned to the criticality of your data and the needs of your business around recovery point objectives (RPO) and recovery time objectives (RTO). Recover the most critical data in the least amount of time.
Finally, just having a strategy is not sufficient. Periodic testing of disaster recovery and business continuity is just as important.
- Encrypted attacks
Having the right enterprise firewall that is able to scan all traffic irrespective of file size is also critical. With the rapid increase in SSL encrypted traffic, as indicated by the Dell Security Threat Report, there is always a risk of downloading encrypted malware that is invisible to traditional firewalls. Hence it is important to ensure the firewall/IPS is able to decrypt and inspect encrypted traffic without slowing down the network significantly.
Another recommendation is to show hidden file extensions. For example, sometimes malware can enter the system with a .pdf or .mp3 icon, but in reality it is an .exe file.
- Monitoring and management
The enterprise firewall should be able to monitor both incoming and outgoing traffic, and block communication with blacklisted IP addresses as ransomware tries to establish contact with its command and control servers.
If a ransomware infection is detected, disconnect the infected system immediately from the corporate network. As soon as a new malware variant is detected, the firewall should have an automated update and centralized management process to roll out updates and policies quickly and consistently across all nodes. In addition, it is crucial to update your software and operating systems regularly.
Conclusion
Dell Security solutions can enhance protection across your organization by inspecting every packet and governing every identity. As a result, this protects your data wherever it goes, and shares intelligence to safeguard against a variety of threats, including ransomware.
Learn more about SonicWall next-generation firewalls by contacting ITG, info@itgcorporation.com or 518.694.8053.
![]()
© 2017 SonicWall Inc. ALL RIGHTS RESERVED.
SonicWall is a trademark or registered trademark of SonicWall Inc. and/or its affiliates in the U.S.A. and/or other countries. All other trademarks and registered trademarks are property of their respective owners.
PROTECT YOUR INFORMATION

The threat against our private and business information has never been as serious as it is today, but measures can be taken to avert those threats. Think of your private information in the same context as your personal belongings: if you leave your car unlocked in a large parking lot you’re taking a chance that anything left inside will be missing upon your return. But belongings, though perhaps having sentimental value, can be replaced. Information however, whether personal or business, cannot be replaced and its theft can lead to a mountain of debt and hours of time involved in rectifying the loss.
Security is second nature to ITG, which is why we are taking this opportunity urging you to take action now to protect your personal and business information. If you follow these simple recommendations you can help protect this sensitive information. Though these recommendations are focused on the corporate environment, they are just as effective for your home computer and you are encouraged to adopt.
- Change your passwords. This includes the password to log into your computer, and any sensitive websites that you have accounts with.
- Select passwords you can commit to memory rather than writing them down.
- Lock your computer (press CTRL ALT DELETE on the keyboard and choose “lock this computer”) when not at your desk.
- Be alert to any strange emails that you may receive. If you are unsure, feel free to contact ITG for assistance at info@itgcorporation.com or by calling 518.694.8053.
- If anything seems strange on your computer at any time, alert someone.
Consider these password changes:
- A good rule of thumb is to set a policy requiring a password change every 90 -180 days.
- It is recommended that password requirements meet the standards of:
- 8 – 12 characters
- at least one each of UPPERCASE, lowercase and number or symbol
Note that the longer the password, the more difficult it will be to hack.
Contact us if you have any questions on network or email security, info@itgcorporation.com or 518.694.8053. Together, we can ensure a more secure environment.

